Cyber Security
The practice of technologies, processes and controls to protect systems, networks, programs, devices and data from cyber attacks. CyberQuote has leading Cyber Security Services in Singapore & South East Asia in countries like Hong Kong, Thailand, Turkey, Japan and Indonesia.


Two-Factor Authentication
Provides two-factor authentication solution for your commercial networks to protect your data security.

Cyber Security Solutions
Provide data, information, analytics and cyber security services to businesses, including but not limited to Vulnerablility Assessment, Penetration Testing.

Cyber Safeguard Awareness Programme
Provides two-factor authentication solution for your commercial networks to protect your data security.
- Two-Factor Authentication
- Cyber Security Solutions
- Cyber Safeguard Awareness
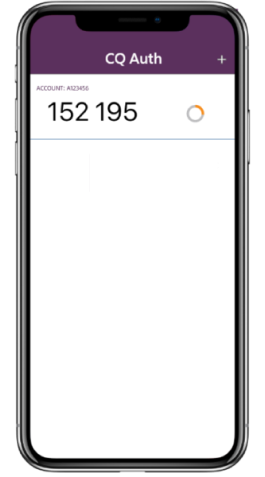
Two-Factor Authentication (2FA)
The best way to protect your account
Provide data, information, analytics and cyber security services to businesses, including but not limited to Vulnerablility Assessment, Penetration Testing.
Reasons to choose 2FA Solution
Competitive Price
Affordable monthly cost.
Easy to install
Provides 2FA API interface. Easily connect to any third-party system.
24/7 Technical Support
Worldwide technical team provides technical support anytime anywhere
Customizable application
Develop 2FA application according to your needs
Features

Provide a 6-digit one-time password valid for 30 seconds

Use QR Code to add accounts easily

Multiple accounts to register and use

Simple interface

Offline usage available



Cyber Security Solutions
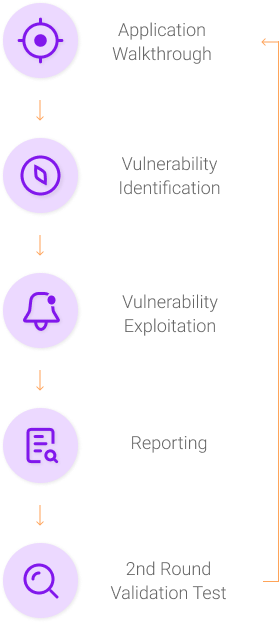
Penetration Testing
Is your IT infrastructure secure against hackers? You have installed the necessary firewalls just last month but since then hackers may have continued to search for vulnerabilities in your system, probing and testing for security gaps and lapses.
Finding any new vulnerabilities by having ethical professionals conduct Penetration Tests on your system and have the security gaps patched and sealed before the hackers find them.
It is absolutely necessary to find any new vulnerabilities before the hackers do.
It is absolutely necessary to find any new vulnerabilities before the hackers do.
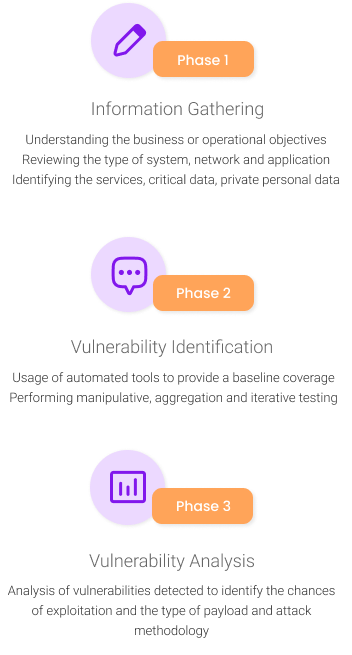
Vulnerability Assessment
Vulnerability Assessment is a risk management process used to identify, quantify and rank possible vulnerabilities to threats in cyber security. The vulnerability assessment methodology combines both black box and white box approach.
Reveal vulnerabilities
Explores existing weaknesses in your system or application configurations and network infrastructure
Show real risks
What an attacker could do in the ‘real world’ can be revealed
Test your cyber-defence capability
Detect attacks and respond adequately and on time
Ensure business continuity
Ensure that your operations don’t suffer from unexpected downtime or a loss of accessibility
Have a third party expert opinion
Report from a third-party expert often has a bigger impact on your management
Follow regulations and certifications
Conduct regular penetration tests and security reviews to ensure legal compliance

Cyber Safeguard Awareness Programme
Increase the level of user awareness
Commercial enterprises that rely extensively on their online databases cannot undermine the importance of Cyber Security. Unless you deploy a proven measure to safeguard your sensitive data you can never know when hackers can malign their integrity. Cyber-Safeguard Awareness Programme (C-SAP) training is esstential for corporate staff.
C-SAP is a Tailored-Programme to ensure your staff are aware of
cyber security threats that would be detrimental to your organisation.
C-SAP is a Tailored-Programme to ensure your staff are aware of
cyber security threats that would be detrimental to your organisation.

e-Learning User
Awareness

Simulated Ethical
Phishing Attack